Welcome to a detailed exploration of Zeeroq, a platform at the heart of modern data management and, unfortunately, a significant data breach. In our digital age, understanding the mechanisms and repercussions of data breaches is not just useful—it’s essential. This post will guide you through what Zeeroq is, the details of its major data breach, and how such events shape data security measures. By the end, you’ll have a comprehensive understanding of Zeeroq’s role in data security and practical advice to protect your personal information in an increasingly connected world.
Table of Contents
What is Zeeroq?
Zeeroq operates as a dual-purpose platform, known for its robust data analytics capabilities and a darker role as a repository for data breaches. Originally designed to provide businesses with a secure method to manage and analyze large datasets, Zeeroq also became infamous when hackers started using it to store and exchange stolen data. This dual nature makes understanding Zeeroq crucial for anyone dealing with data management or concerned about personal data security.
While the platform offers advanced tools for data integration, governance, and visualization aimed at enhancing business decisions, its name is often associated with significant security breaches. The complexity of Zeeroq’s infrastructure, meant to safeguard data, ironically has also been a point of vulnerability, exposing users to potential risks and losses. This dichotomy is essential to grasp as we delve deeper into the specifics of the data breach incident that brought Zeeroq into the spotlight.
The Zeeroq Data Breach Explained
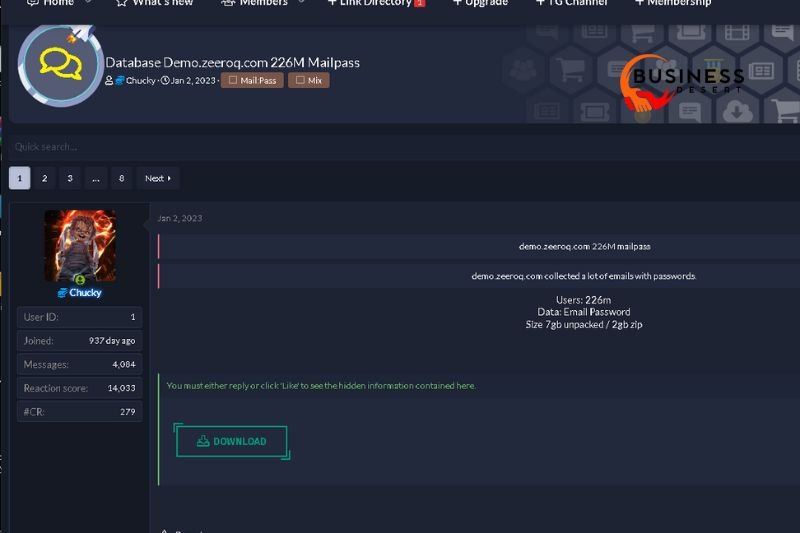
In early 2023, Zeeroq reported a massive data breach that compromised sensitive information of thousands of users. This breach was traced back to a vulnerability in a third-party library used by the platform, which hackers exploited to access the cloud storage services where Zeeroq stored its data. This incident highlighted the ever-present risks in digital data management and raised concerns over the security measures in place at Zeeroq.
The breach resulted in the leak of personal identifiable information (PII), financial details, and login credentials, affecting over 100,000 individuals and businesses. The fallout was immediate, with users experiencing unauthorized transactions and identity theft. The scale and severity of this breach serve as a case study on the potential impacts of cybersecurity failures in modern digital platforms.
How Does Zeeroq Work?
Zeeroq’s functionality is centered around its ability to offer a secure environment for storing and managing data across various sectors. By using advanced encryption methods and compliance protocols, Zeeroq promises to keep user data safe from unauthorized access. However, the breach exposed critical flaws in these protective measures, showing that no system is entirely immune to cyber threats.
The platform employs a range of security features, including regular audits, real-time threat detection, and automated compliance checks. These systems are designed to safeguard data from common cyber threats and ensure that all data management complies with the latest security standards. Understanding these mechanisms is key to recognizing where things went wrong during the breach and how similar incidents can be prevented in the future.
The Aftermath of the Zeeroq Breach
Following the breach, Zeroq took immediate steps to mitigate the damage, including notifying affected users and offering free credit monitoring services. The company also implemented stronger security measures, such as updating their encryption practices and increasing their cybersecurity team. These actions were crucial in restoring trust and securing the platform against future attacks.
The long-term effects of the breach are still being felt as Zeroq continues to overhaul its security protocols. The incident has spurred a broader discussion on the need for rigorous data protection laws and has made data security a top priority for similar platforms. By learning from Zeroq’s response, other companies can better prepare and potentially prevent such breaches on their own systems.
Protecting Yourself from Data Breaches
Data breaches like the one at Zeroq can have devastating effects, making it essential for individuals to take proactive steps to protect their personal information. Firstly, always monitor your financial accounts for any unusual activities. Early detection of fraud can significantly minimize damage. Additionally, using strong, unique passwords for different accounts and enabling two-factor authentication wherever possible can help secure your online presence.
Another effective strategy is to regularly update your software and devices to protect against known vulnerabilities. Hackers often exploit outdated systems, so keeping your technology current is a simple yet effective defense. Awareness and education about phishing tactics and other common cyber scams are also critical, as these are frequently used to gain unauthorized access to personal information.
The Future of Data Security with Zeeroq
As we look to the future, Zeroq is poised to play a significant role in shaping the landscape of data security. The lessons learned from its breach are leading to innovations in cybersecurity measures and protocols. Businesses and individuals alike are now more aware of the risks and are implementing more stringent security measures to protect their data.
The evolution of data security practices, driven by incidents like the Zeroq breach, is likely to emphasize transparency and user control over personal information. As technology advances, so too will the methods to protect it, likely incorporating more artificial intelligence and machine learning to predict and counteract threats before they can cause harm. For Zeroq and its users, the future promises greater security awareness and improved practices that could set new standards for data protection in the digital age.
Conclusion
The Zeeroq data breach serves as a crucial reminder of the vulnerabilities inherent in managing and storing data digitally. It underscores the importance of robust cybersecurity measures and the need for ongoing vigilance in protecting sensitive information. By understanding the complexities of Zeroq and similar platforms, users can better navigate the risks and take appropriate actions to safeguard their personal and professional data.
For More Visit : Businessdesert